Why GRASP?
Three reasons for our software solution GRASP
1. Capture, visualize and communicate risks in an understandable way
Follow the risk-based approach: evaluation, treatment and continuous overview of risks.

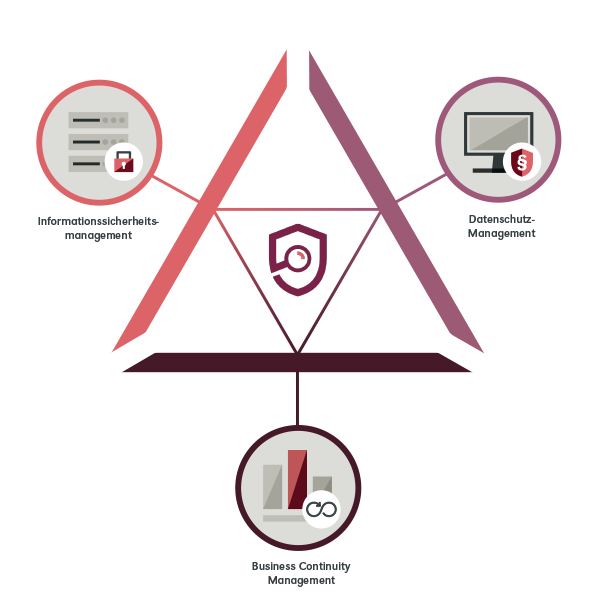
Information Security Management System (ISMS)
With increasing digitalization and growing networking, the potential for threats has risen rapidly. Ignoring both familiar and new IT risks – especially in times of crisis – jeopardizes the economic success and continued existence of the company. An ISMS tool can help to make the company less risky.
Data protection management (DPM)
With the help of the data protection impact assessment (DPIA) and corresponding deletion concepts, you keep your data under control.

Business Continuity Management (BCM)
GRASP guides you through business impact and risk analysis in accordance with ISO 22301 based on the applicability of the standard areas. Then develop solution options and establish BC plans for sustainable business continuation.
Your management system
GRASP stands for Governance, Risk, Audit, Security Platform and enables your organization to digitalize your processes easily and quickly: Thanks to its user-friendly interface, well thought-out user guidance, workflows and easy-to-create reports, GRASP can massively relieve project managers as an ISMS tool, data protection software solution or BCM tool. GRASP enables you to efficiently manage your organization in terms of information security, business continuity and data protection.
Benefit from our approach of an integrated management system, e.g. through a one-time inventory of structures, processes, assets, systems and applications. For example, with our interface to our ITFM solution CIO COCKPIT, you can automatically import your hardware assets into GRASP and immediately evaluate them under aspects of BCM and ISM.
Creating synergy effects
Both BCM, data protection and ISMS use the same database and the same technologies. Your advantage: Expand your portfolio with additional management systems as needed. The multitenant authorization system is taken into account equally in all application areas. Authentication to the system can also be done via your own authentication providers (LDAP, Azure AD, etc.). Workflows enable a high degree of automation options. In our integrated management system, we follow the specifications of ISO standards as far as possible. In addition, we offer the possibility for you to tailor and adapt this standard to your needs.